Posts
Showing posts from 2012
Shibboleth SP part 4 (MediaWiki Configuration)
- Get link
- X
- Other Apps
Shibboleth SP part 3 (Moodle & Wordpress Configuration)
- Get link
- X
- Other Apps
Shibboleth SP part 2 (Typo3 Configuration)
- Get link
- X
- Other Apps
Shibboleth IdP SLO part 3 (Configuration)
- Get link
- X
- Other Apps
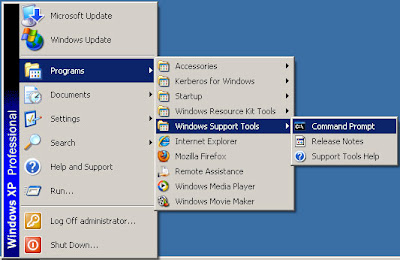
Mapping Kerberos principal to existing eDirectory user
- Get link
- X
- Other Apps
Single Sign On (SSO) with Novell Client and Shibboleth
- Get link
- X
- Other Apps
Shibboleth IdP SLO part 2 (Installation)
- Get link
- X
- Other Apps
Shibboleth IdP SLO part 1 (preparation)
- Get link
- X
- Other Apps
Build Single Sign On Implementation (using computer login) for Intranet or Campus network.
- Get link
- X
- Other Apps